Expert Assignment Solutions with 100% Guaranteed Success
Get Guaranteed success with our Top Notch Qualified Team ! Our Experts provide clear, step-by-step solutions and personalized tutoring to make sure you pass every course with good grades. We’re here for you 24/7, making sure you get desired results !
We Are The Most Trusted
Helping Students Ace Their Assignments & Exams with 100% Guaranteed Results
Featured Assignments
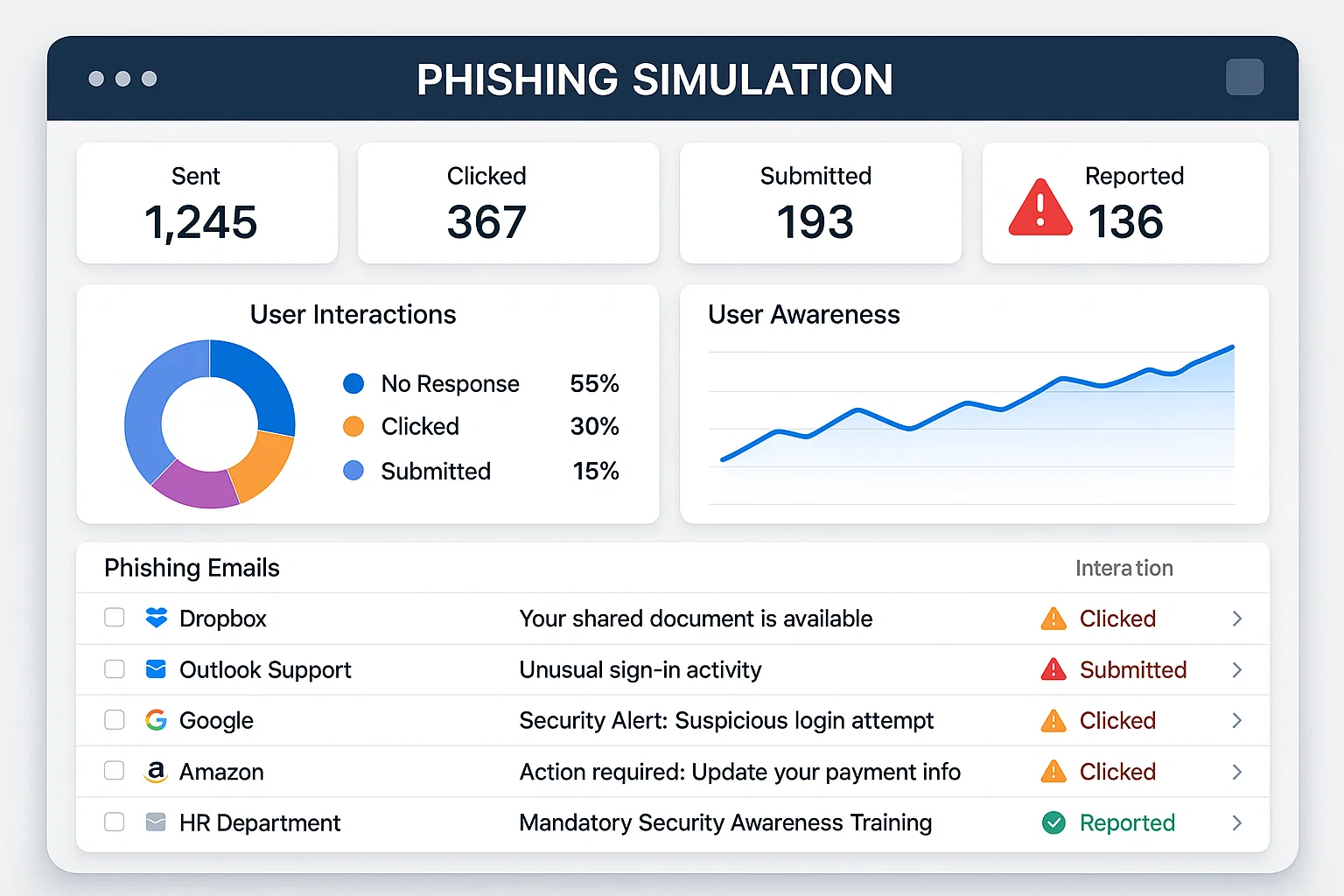
Phishing Simulation and Awareness Campaign
Cybersecurity AwarenessClient Requirements
The student needed to design and implement a phishing simulation tool aimed at educating users about identifying and avoiding phishing attacks. The tool should generate realistic phishing emails and track user interactions to assess their awareness and response to phishing attempts.
Challenges Faced
We ensured the phishing simulations were realistic and varied to effectively mimic actual phishing attacks. The complexity lay in creating diverse scenarios that could accurately assess user responses. Additionally, tracking user interactions required integrating analytics tools to monitor and report on user behavior.
Our Solution
We developed a web-based application that simulates phishing attacks, including spear-phishing and social engineering tactics. The tool was equipped with analytics to monitor user interactions and generate reports on their responses. This approach provided valuable insights into user awareness levels and areas needing improvement.
Results Achieved
The implementation of the phishing simulation tool led to a significant increase in user awareness and a reduction in the number of successful phishing attempts. Users demonstrated improved ability to identify and respond to phishing threats, enhancing overall organizational security posture.
Client Review
Collaborating with them on this project was a transformative experience. The phishing simulation tool they developed was not only technically sound but also user-friendly, making it accessible to individuals with varying levels of cybersecurity knowledge. Their attention to detail and commitment to enhancing user awareness were evident throughout the project.
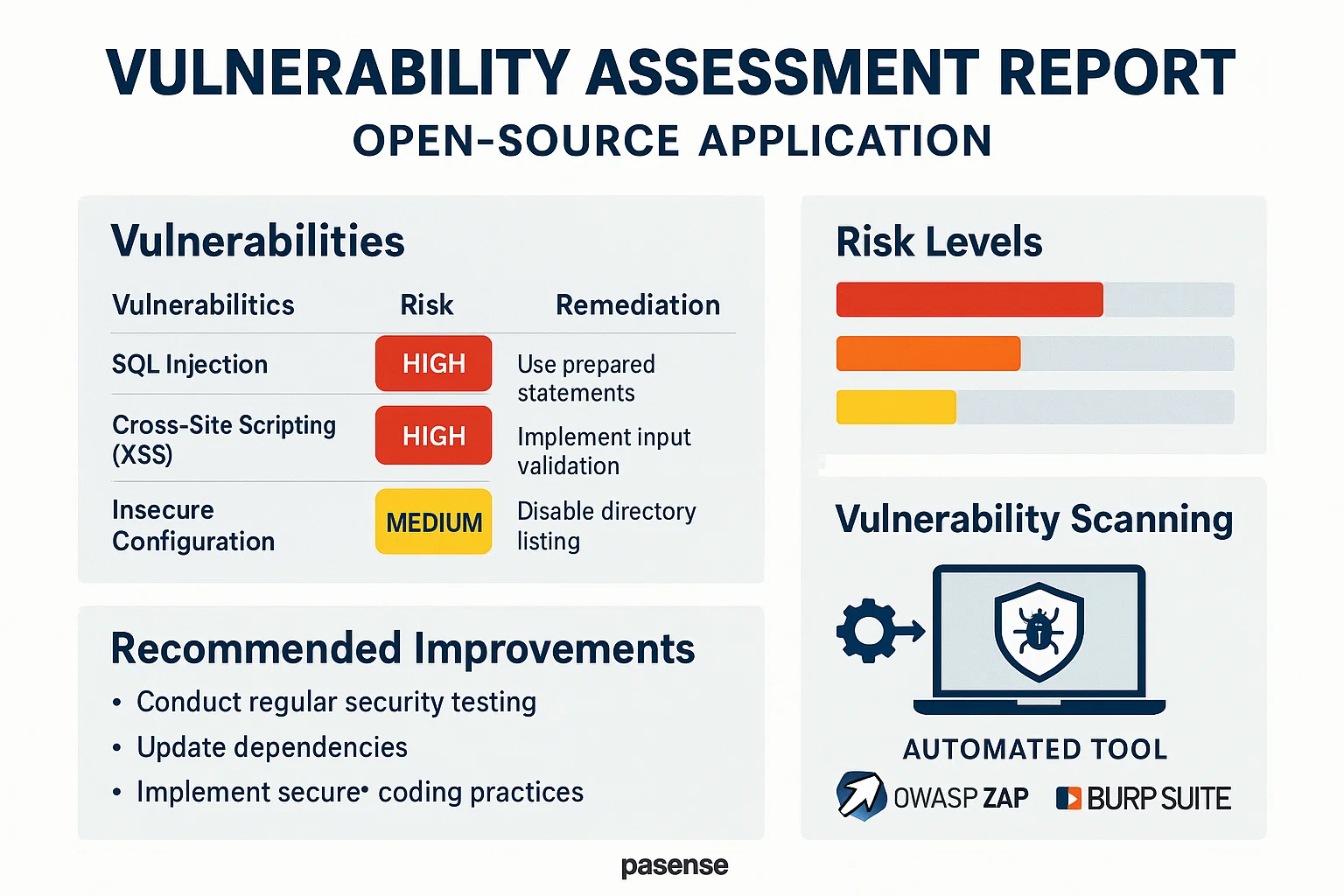
Vulnerability Assessment of an Open-Source Application
Application SecurityClient Requirements
The student wanted to conduct a thorough vulnerability assessment of an open-source application, documenting findings and recommending improvements. The assessment should identify weaknesses such as SQL injection, cross-site scripting (XSS), and insecure configurations.
Challenges Faced
We faced some complications handling the vast array of potential vulnerabilities within the application. Prioritizing which vulnerabilities to address first required a careful risk assessment. Additionally, ensuring that the remediation plans were practical and effective posed a challenge.
Our Solution
We utilized tools like OWASP ZAP and Burp Suite to perform automated scans, followed by manual testing to identify vulnerabilities. A comprehensive report was created, detailing each vulnerability's risk level and providing a step-by-step remediation plan. This approach ensured that the findings were actionable and aligned with best security practices.
Results Achieved
The vulnerability assessment uncovered several critical security flaws within the application. Implementing the recommended changes significantly enhanced the application's security, reducing its susceptibility to common attacks and improving its overall integrity.
Client Review
Their meticulous approach to vulnerability assessment was impressive. The detailed report they provided not only identified critical security flaws but also offered clear and actionable solutions. Their expertise in utilizing industry-standard tools and methodologies was evident, and the improvements made to the application have substantially strengthened its security.
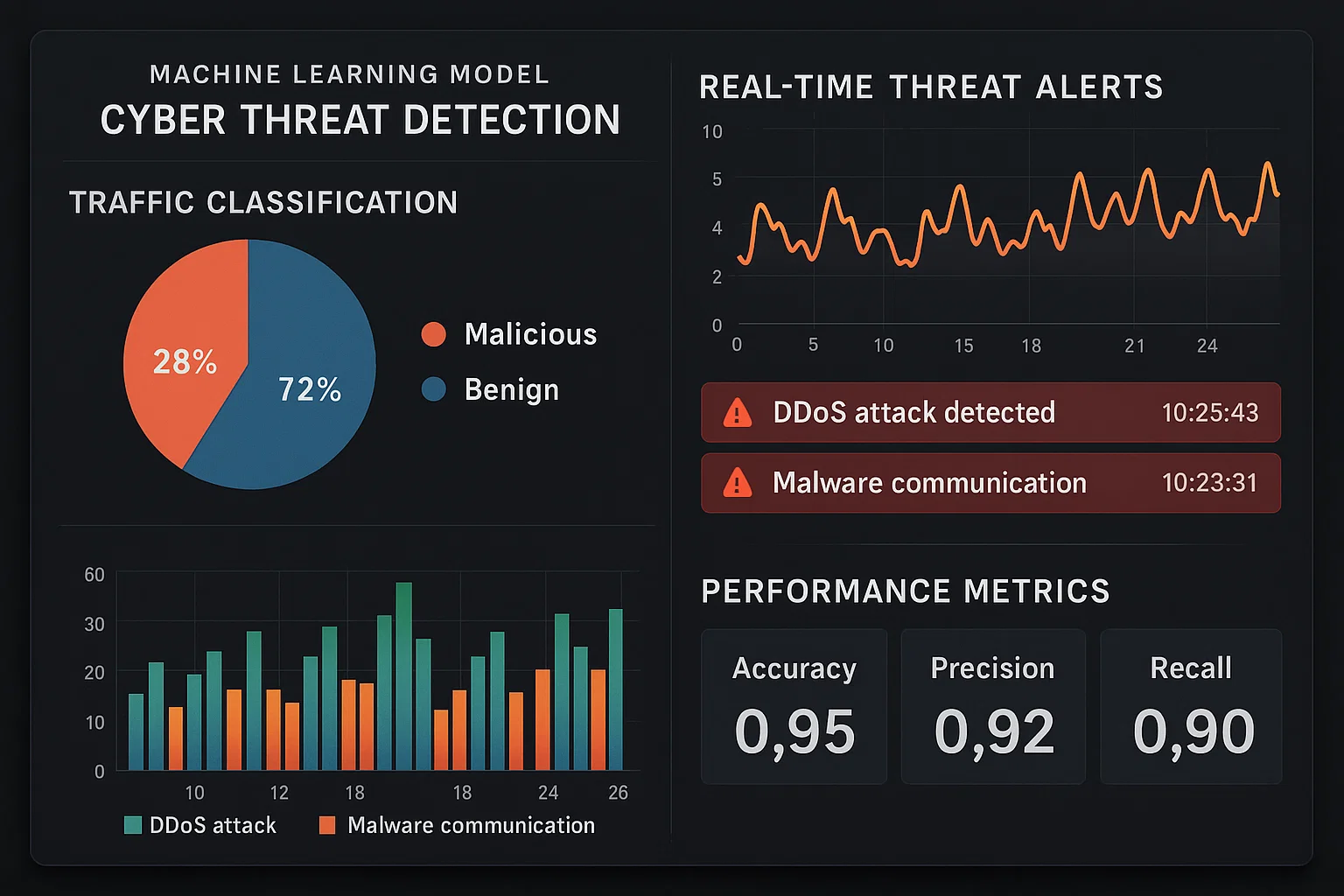
Machine Learning-Based Cyber Threat Detection
Machine Learning in CybersecurityClient Requirements
The student wanted to develop a machine learning model to detect potential cybersecurity threats in network traffic. The model should be trained on a dataset containing both benign and malicious traffic, utilizing various ML techniques for classification.
Challenges Faced
We ensured the dataset was balanced to prevent model bias, which could skew detection capabilities. Handling the high dimensionality of network traffic data required feature selection techniques to improve model performance. Additionally, fine-tuning the model to achieve optimal accuracy without overfitting was a complex task.
Our Solution
We employed algorithms like Random Forest and Support Vector Machines to classify network traffic. Feature engineering techniques were applied to reduce dimensionality, and cross-validation methods were used to assess model performance. The model was iteratively refined to enhance accuracy and minimize false positives.
Results Achieved
The machine learning model demonstrated a high detection rate for various cyber threats, including DDoS attacks and malware communications. Its implementation allowed for real-time threat detection, significantly improving the organization's ability to respond to security incidents promptly.
Client Review
Working with them on this project was a rewarding experience. The machine learning model they developed for cyber threat detection was both innovative and effective. Their ability to navigate the complexities of network traffic data and apply advanced ML techniques resulted in a solution that greatly enhanced our threat detection capabilities.
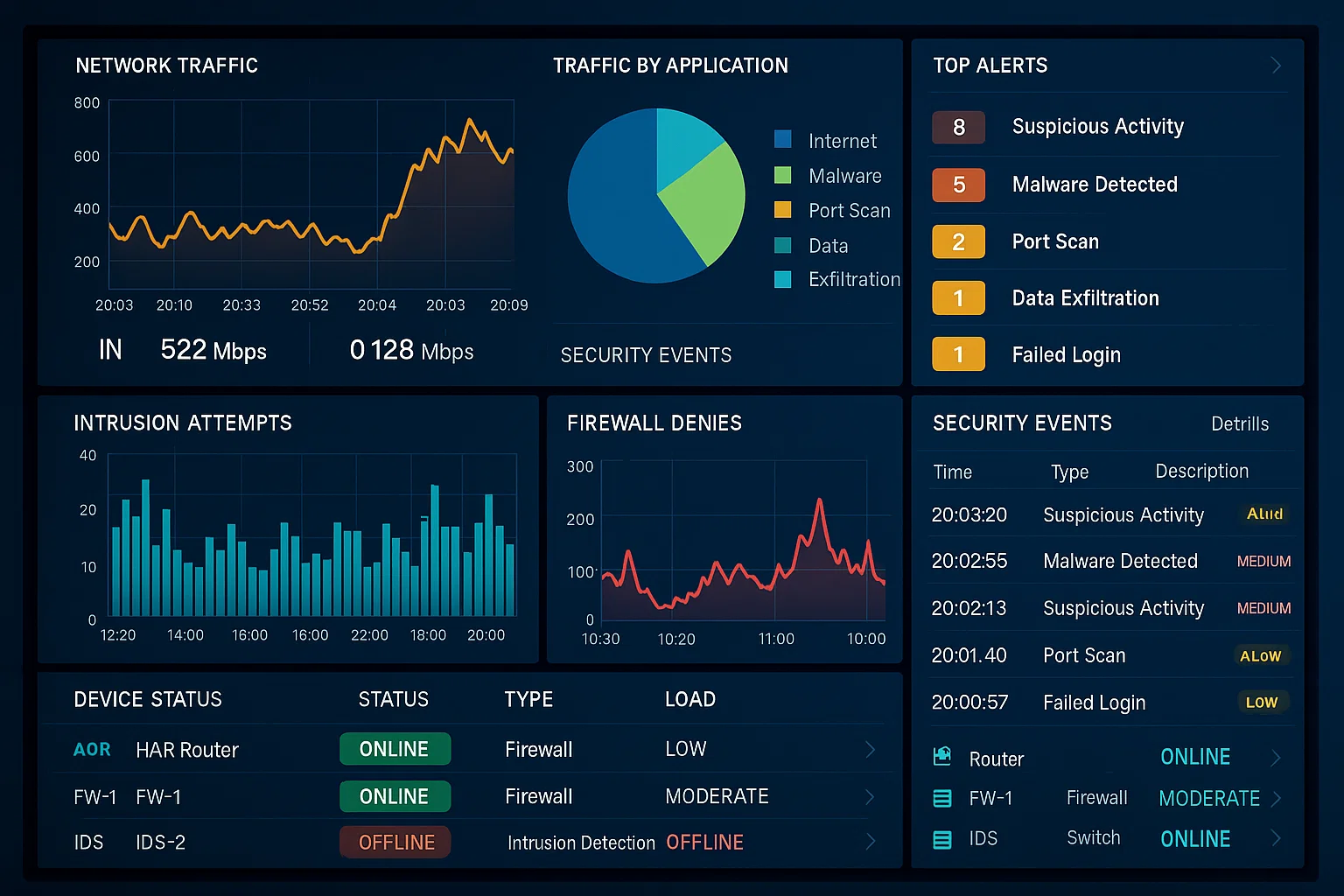
Development of a Real-Time Network Security Monitoring Dashboard
Network Security MonitoringClient Requirements
The student wanted to develop a real-time dashboard that visualizes network activity and alerts users to potential cyber threats. The dashboard should integrate data from network devices like firewalls and intrusion detection systems, providing an intuitive interface for monitoring.
Challenges Faced
We faced some complications handling the integration of diverse data sources, each with its own format and protocol. Ensuring the dashboard's real-time performance under heavy network traffic loads required optimization techniques. Additionally, designing an intuitive user interface that effectively displayed complex data posed a challenge.
Our Solution
We utilized tools like Grafana and Kibana to create a dynamic dashboard capable of ingesting data from various network devices. Real-time data processing pipelines were implemented to ensure timely updates. The user interface was designed with user experience in mind, presenting data in a clear and actionable manner.
Results Achieved
The network security monitoring dashboard provided a comprehensive view of network activity, enabling security teams to identify and respond to threats more efficiently. Its real-time capabilities allowed for proactive threat management, reducing the potential impact of security incidents.
Client Review
Their work on the network security monitoring dashboard was exceptional. The dashboard's real-time capabilities and intuitive design have significantly improved our ability to monitor and respond to network threats. Their technical expertise and attention to user experience were key factors in the project's success.
