Expert Assignment Solutions with 100% Guaranteed Success
Get Guaranteed success with our Top Notch Qualified Team ! Our Experts provide clear, step-by-step solutions and personalized tutoring to make sure you pass every course with good grades. We’re here for you 24/7, making sure you get desired results !
We Are The Most Trusted
Helping Students Ace Their Assignments & Exams with 100% Guaranteed Results
Featured Assignments
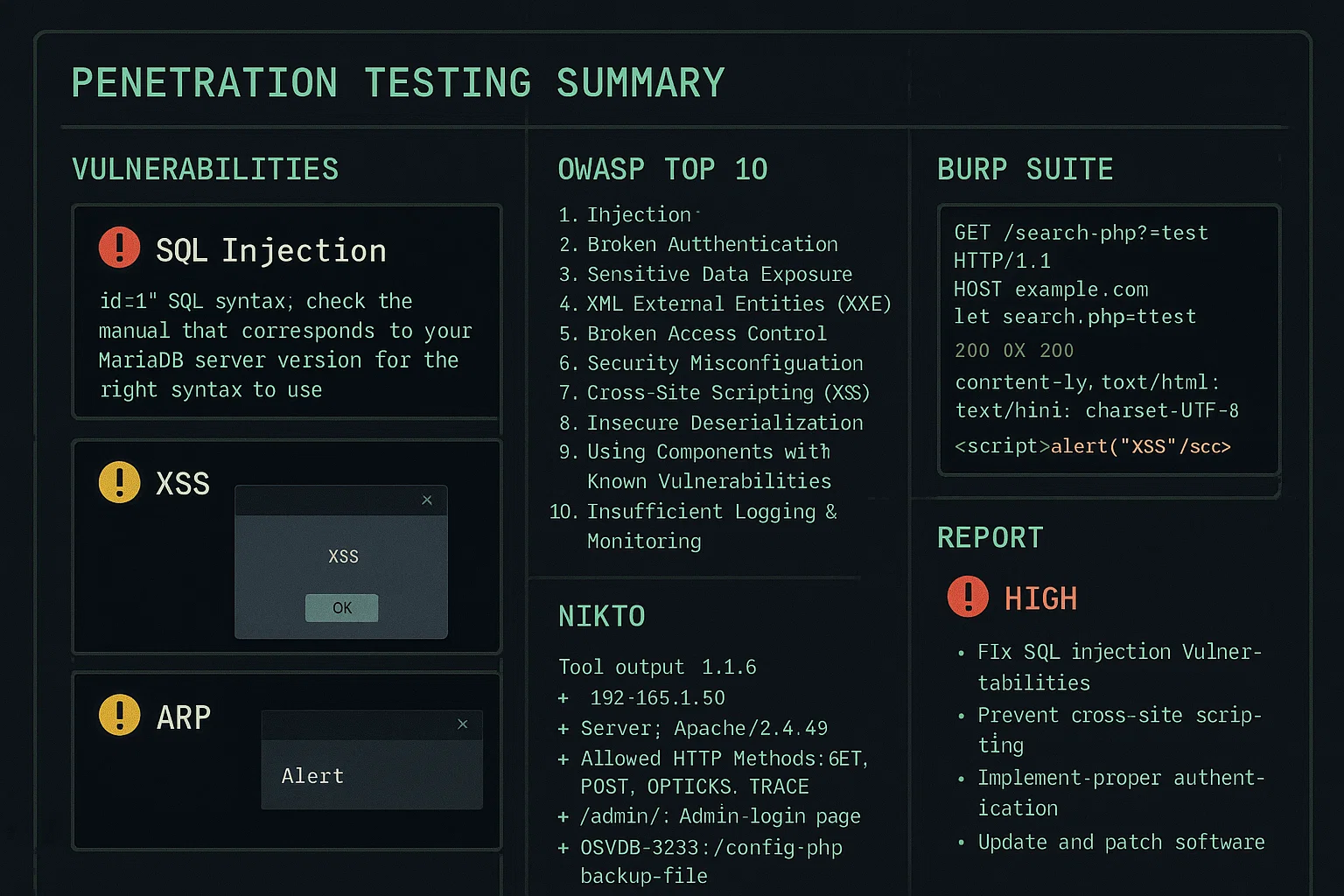
Penetration Testing Simulation Using Kali Linux and OWASP Top 10
Cybersecurity & Penetration TestingClient Requirements
The student wanted to develop a realistic penetration testing report for a mock web application. Their focus was on practicing exploitation techniques and generating detailed documentation based on OWASP Top 10 vulnerabilities using Kali Linux tools.
Challenges Faced
We ensured the testing environment was safe and isolated, but faced complications while replicating exploitable vulnerabilities without triggering false positives. Configuring the vulnerable app stack and managing privilege escalation scenarios within the sandboxed setup also demanded caution.
Our Solution
We deployed a DVWA (Damn Vulnerable Web App) on a virtual server, performed active reconnaissance, injection attacks, XSS simulations, and brute-force credential tests using Burp Suite, Nikto, and Hydra. The final report included step-by-step exploit paths, screenshots, impact ratings, and countermeasures for each discovered flaw.
Results Achieved
A professionally structured penetration test report with real attack simulations and mitigation recommendations. It demonstrated the student’s ability to identify, exploit, and responsibly document vulnerabilities.
Client Review
Assignment C.S.101 turned out to be exactly what I was hoping for — the whole testing was realistic, detailed, and felt like real-world red team work. The screenshots, findings, and breakdown of OWASP issues were all properly laid out. I had a really deep and rewarding experience working with them!
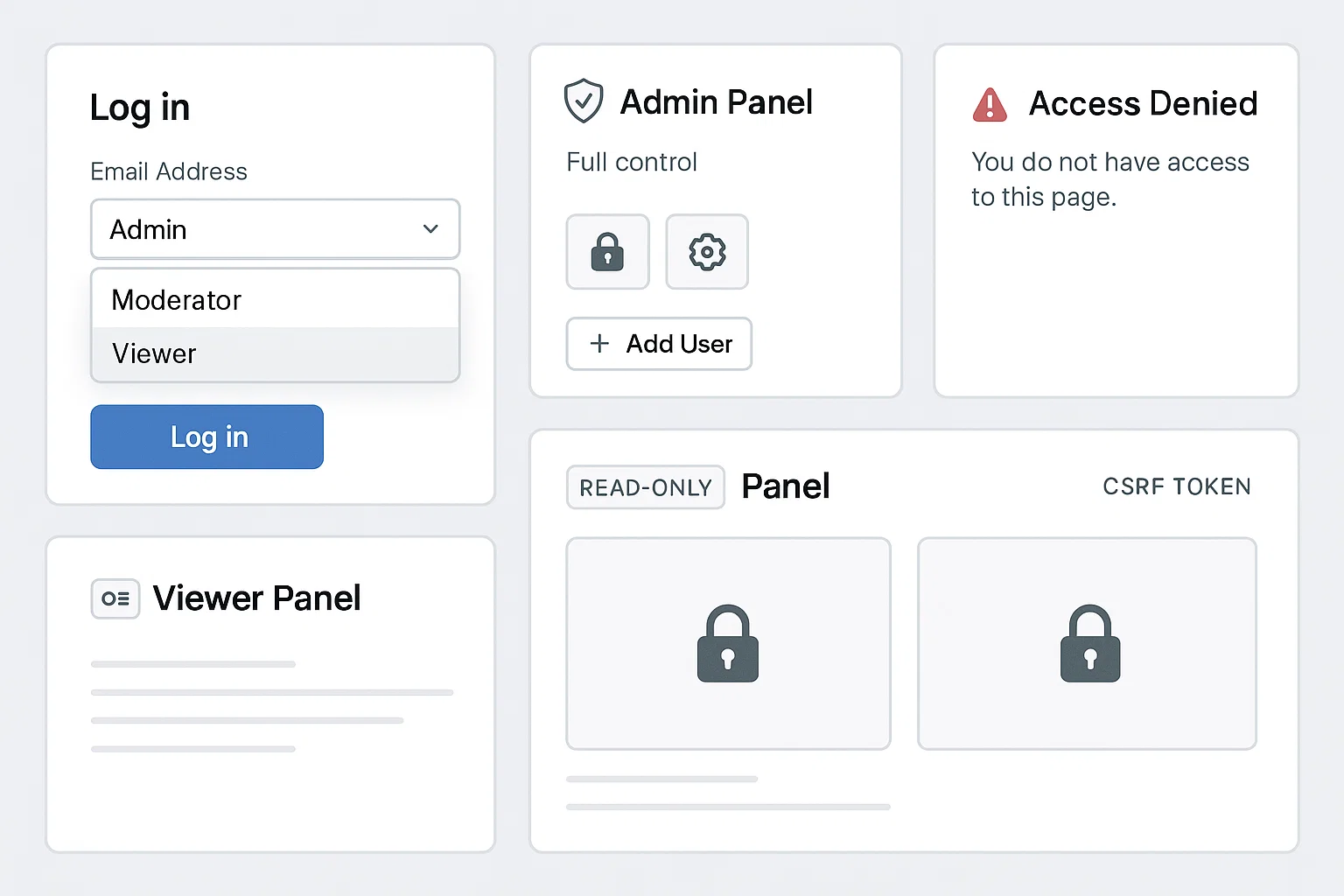
Building a Role-Based Access Control (RBAC) System in a Secure Web App
Web App Security & Access ControlClient Requirements
The student wanted to build a web application with multi-level secure access control, where users (admin, moderator, viewer) had restricted functionalities. They aimed to showcase RBAC implementation, session management, and protection against unauthorized access.
Challenges Faced
We ensured user sessions were properly handled, but faced complications dealing with session hijacking risks and keeping privilege escalation under control. Creating dynamic route guards and protecting backend endpoints from bypasses was especially tricky.
Our Solution
We developed a Flask-based web app with user roles stored in a database, encrypted sessions, and custom decorators to restrict routes based on user roles. Middleware checked tokens, logged sessions, and blocked unauthorized page access. We also implemented CSRF tokens and password hashing for extra protection.
Results Achieved
A secure, functional app with perfectly working RBAC. All roles performed their designated actions with zero leakage, and the code was clean and audit-ready. Security testing passed for multiple attack types.
Client Review
Assignment C.S.202 was a total success. The RBAC logic was tight — I couldn’t access a thing outside my role. The backend was locked down and coded smartly. This felt like a true production-grade implementation. Definitely one of the best experiences I’ve had!
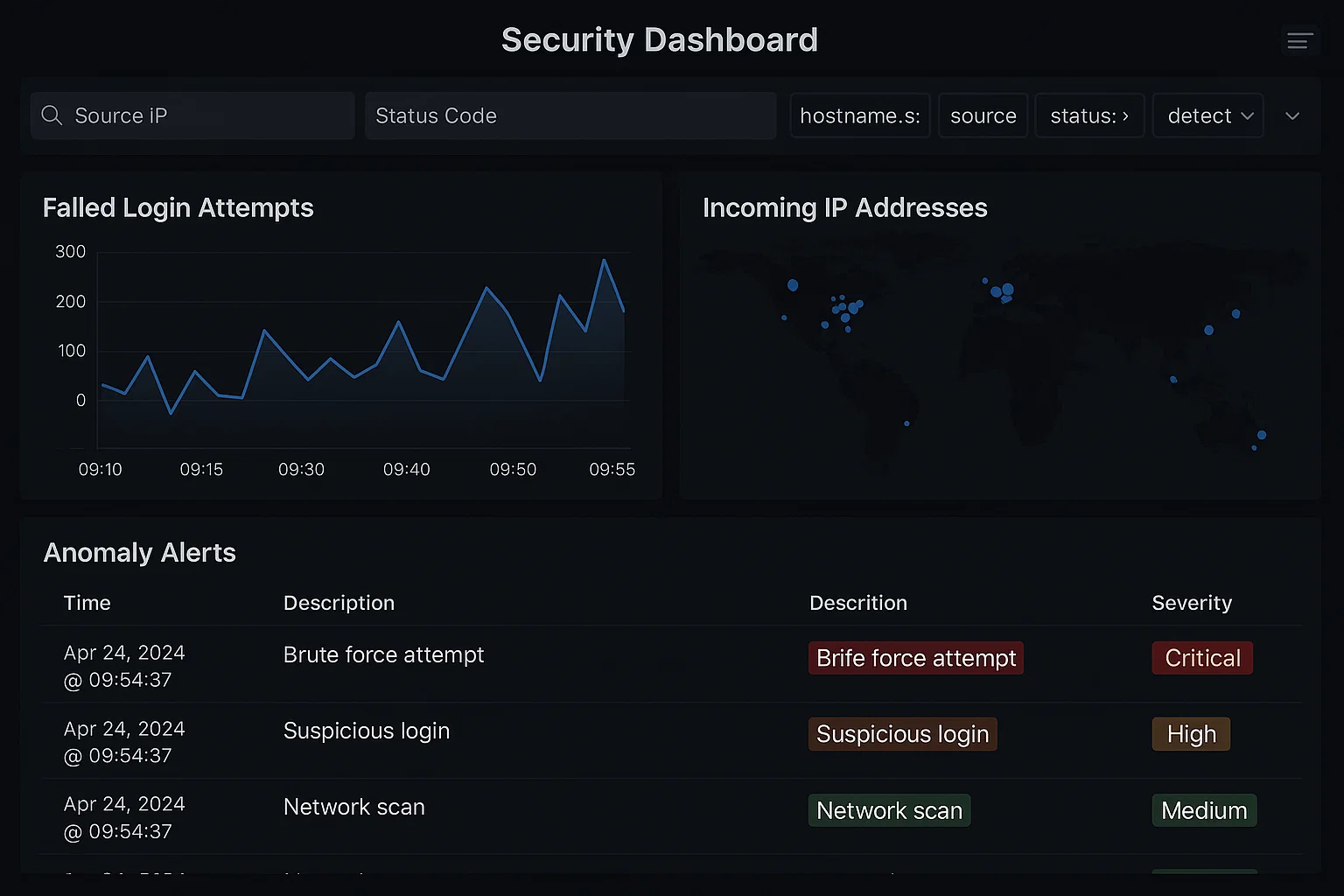
Log Analysis and Anomaly Detection Using SIEM (ELK Stack)
SIEM & Threat DetectionClient Requirements
The student wanted to simulate a Security Information and Event Management (SIEM) use case by performing log analysis and anomaly detection on a network using the ELK Stack (Elasticsearch, Logstash, Kibana).
Challenges Faced
We ensured the pipeline worked seamlessly, but handling high log volumes and visualizing real anomalies (rather than noise) proved challenging. Designing patterns that would reveal port scanning, brute force, or unusual behavior needed custom parsing logic.
Our Solution
We configured a virtual network to generate synthetic log data (auth logs, NGINX logs, firewall entries), routed them through Logstash, indexed in Elasticsearch, and created Kibana dashboards to spot anomalies like suspicious IPs, failed logins, and traffic spikes. Custom alert rules were also defined.
Results Achieved
An intelligent security dashboard with real-time log visualization, anomaly detection logic, and alerts for predefined threat conditions. The student’s understanding of SIEM principles was clearly demonstrated.
Client Review
Assignment C.S.303 was powerful and enlightening. The dashboards, graphs, and alerts worked beautifully, and the insights from raw logs blew me away. It felt like I was sitting in a SOC! Everything was configured with care — truly exceptional experience.
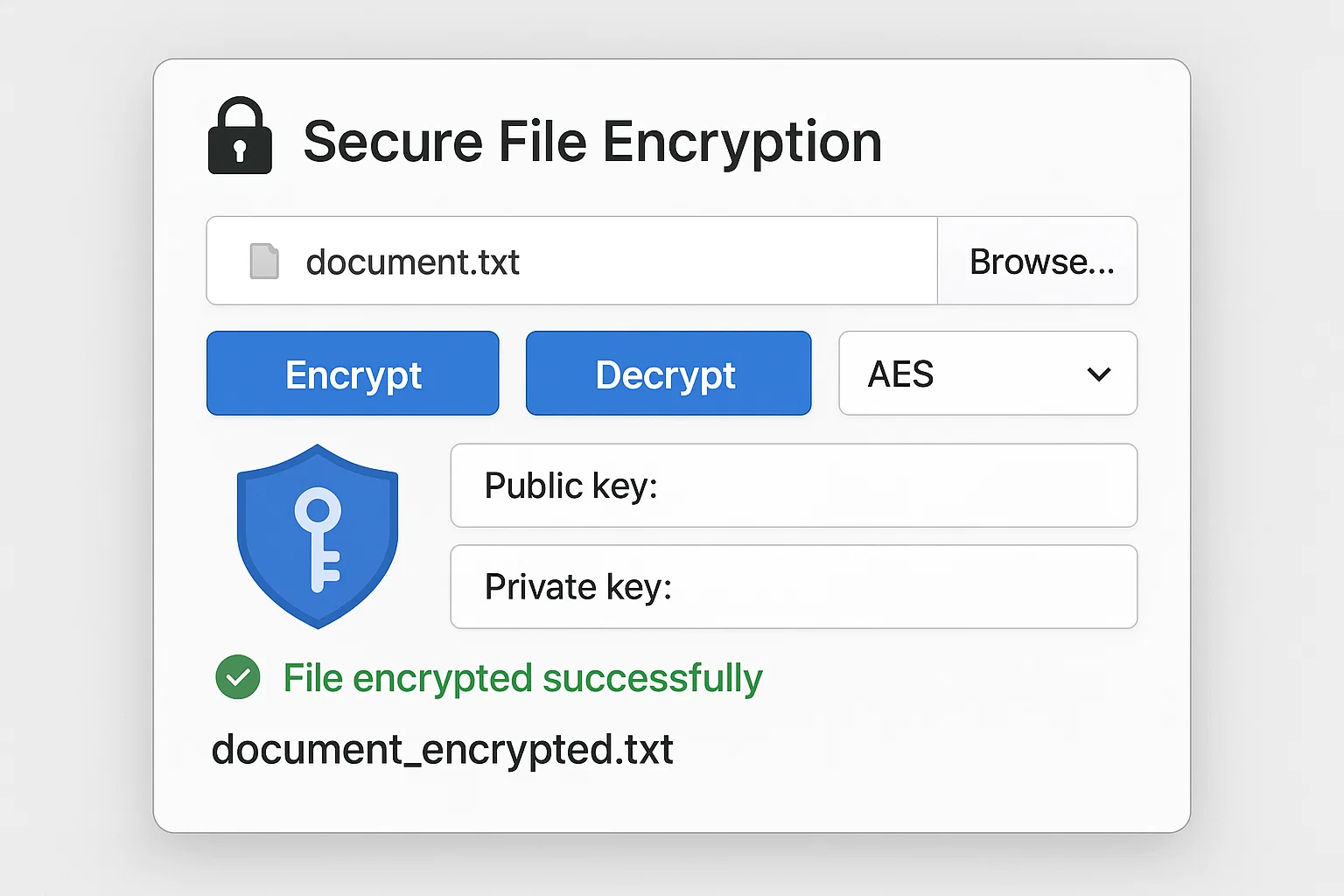
Cryptography-Based Secure File Sharing System with AES & RSA
Applied Cryptography & Secure CommunicationClient Requirements
The student was interested in building a secure file sharing desktop application where users could encrypt and decrypt files using AES for bulk data and RSA for key exchange. The app had to simulate end-to-end encryption for real-world use.
Challenges Faced
We ensured the cryptographic standards were met, but faced challenges with hybrid encryption logic and secure key storage. Handling large file encryption while keeping the GUI responsive required efficient threading and memory management.
Our Solution
We developed a Python-based desktop app using Tkinter for UI, PyCrypto for AES (symmetric) encryption of files, and RSA (asymmetric) for sharing AES keys securely. The interface allowed users to upload, encrypt, download, and decrypt files with auto key generation and exchange.
Results Achieved
A functioning, user-friendly encryption app demonstrating real cryptographic practices. It was able to handle different file types, ensure confidentiality, and simulate secure communication between users.
Client Review
I couldn’t be happier with Assignment C.S.404! The file encryption and decryption worked flawlessly, and the hybrid crypto design was so well thought out. The app looked clean, ran smooth, and proved my concept completely. My experience with them was simply top-tier.
