Expert Assignment Solutions with 100% Guaranteed Success
Get Guaranteed success with our Top Notch Qualified Team ! Our Experts provide clear, step-by-step solutions and personalized tutoring to make sure you pass every course with good grades. We’re here for you 24/7, making sure you get desired results !
We Are The Most Trusted
Helping Students Ace Their Assignments & Exams with 100% Guaranteed Results
Featured Assignments
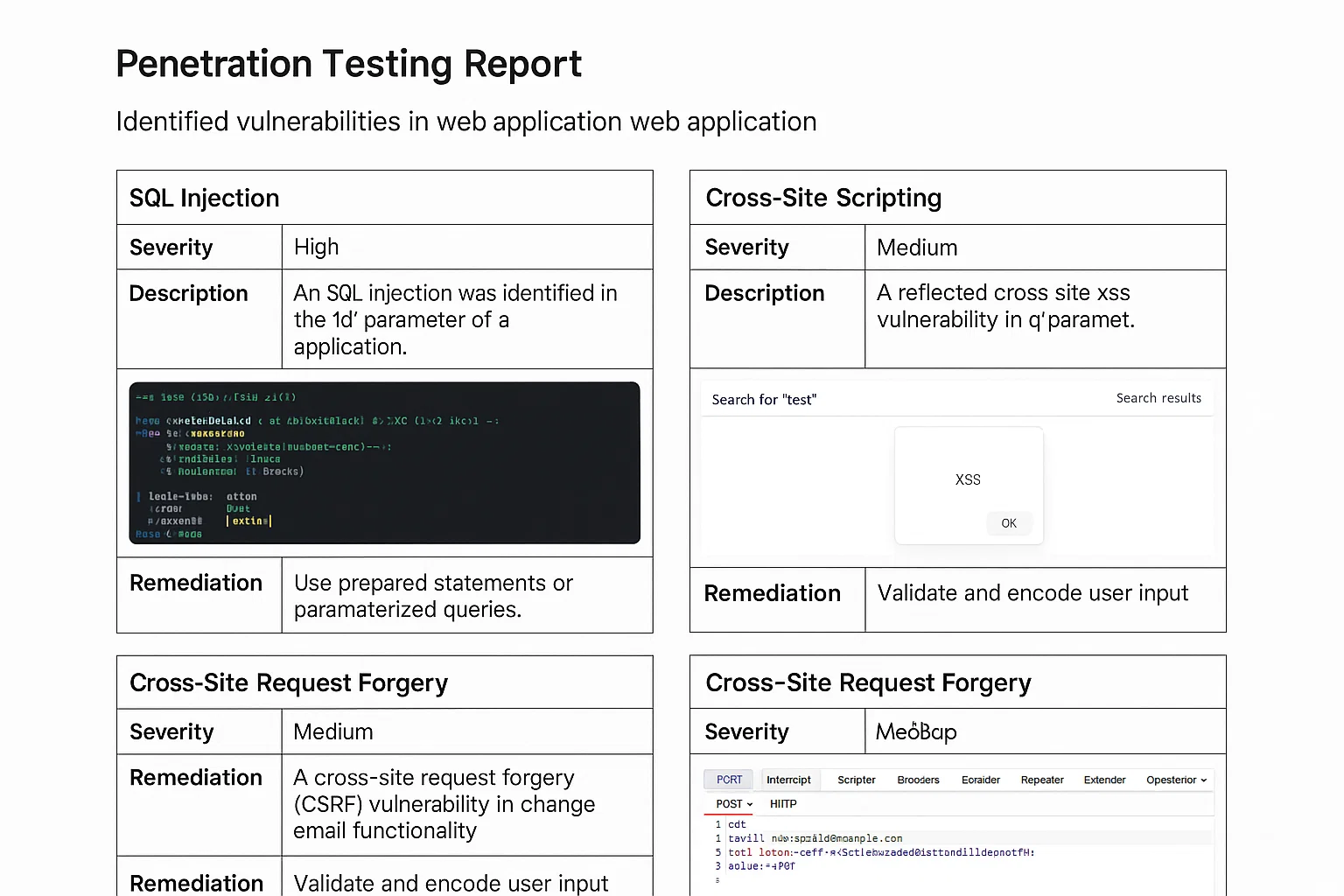
Vulnerability Assessment and Penetration Testing
Ethical Hacking and Penetration TestingClient Requirements
The student needed to conduct a vulnerability assessment and penetration testing on a web application or network. The task required identifying common vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and insecure configurations. The student was also asked to exploit these vulnerabilities in a controlled environment and then provide detailed remediation steps to secure the application or network.
Challenges Faced
We ensured that students understood the ethical boundaries of penetration testing, as some students faced challenges distinguishing between authorized testing and malicious hacking. Some struggled with using tools like Burp Suite, Metasploit, or OWASP ZAP effectively and faced difficulties in simulating real-world attack scenarios while maintaining system integrity. Additionally, understanding the full scope of vulnerabilities in different layers of the application (e.g., application layer, network layer) proved complex for some students.
Our Solution
We provided students with tutorials on setting up penetration testing tools and how to safely test systems for vulnerabilities. We introduced step-by-step guides on identifying and exploiting common vulnerabilities, while emphasizing safe and responsible testing. Students were given access to vulnerable test environments (e.g., DVWA, Hack The Box) where they could practice without risking damage to live systems. Additionally, we provided templates for vulnerability assessment reports, guiding students on how to document findings and suggest solutions.
Results Achieved
The students successfully identified and exploited a variety of vulnerabilities within controlled environments. They provided comprehensive reports with clear descriptions of the vulnerabilities, exploitation methods, and remediation strategies. Most students demonstrated a solid understanding of security principles and were able to present practical solutions for securing web applications and networks.
Client Review
My experience with this assignment was highly educational. The process of conducting penetration testing in a controlled environment was eye-opening, and I gained real-world skills in identifying vulnerabilities. The tools and resources provided helped me conduct thorough assessments, and the remediation strategies I developed gave me a deeper understanding of application security. The hands-on experience was invaluable, and I feel more confident in my ability to secure systems.
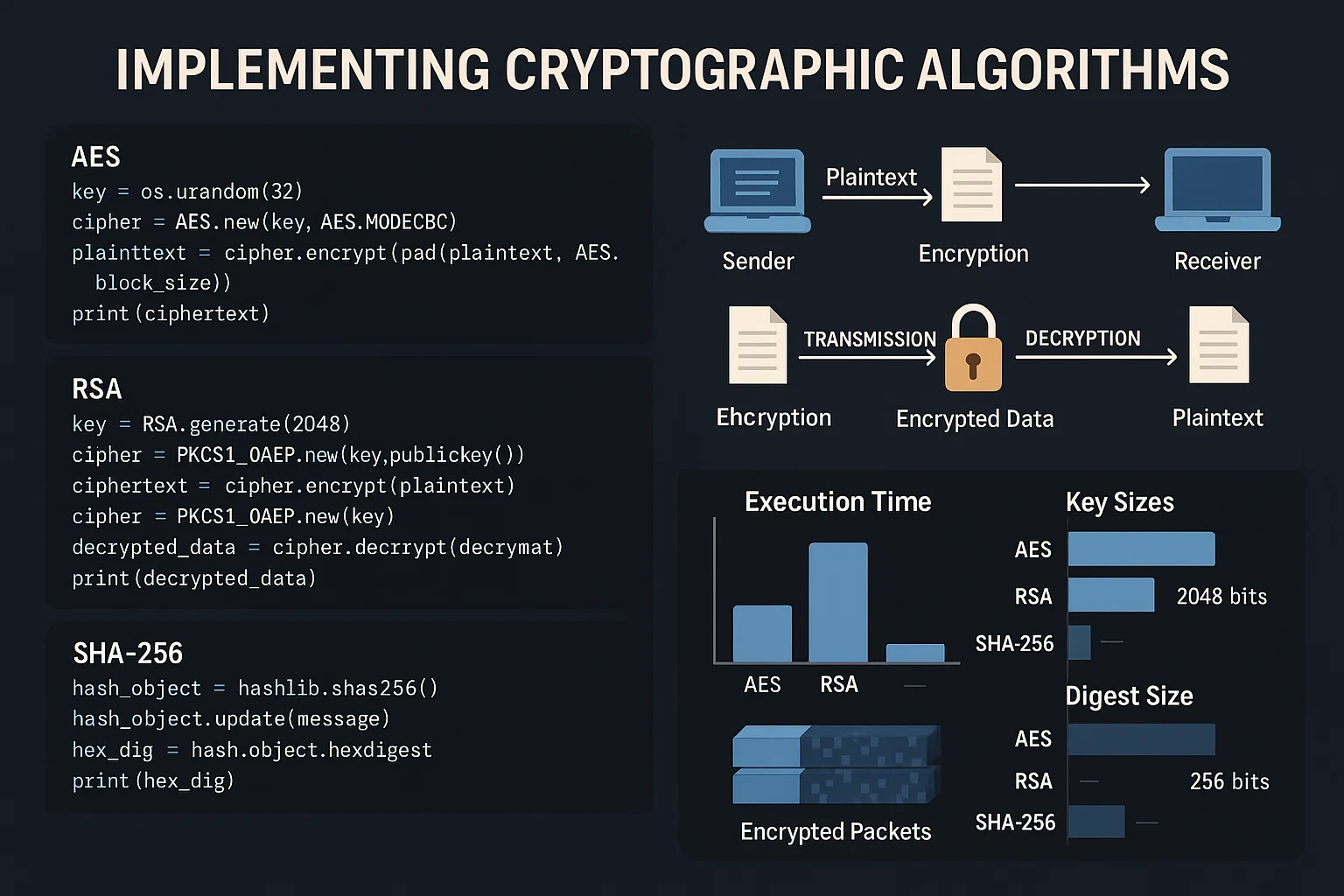
Cryptography Algorithms and Practical Implementation
Cryptography and Network SecurityClient Requirements
The student needed to implement and analyze basic cryptographic algorithms, including symmetric encryption (e.g., AES, DES), asymmetric encryption (e.g., RSA), and hashing algorithms (e.g., SHA). The task required the student to develop code to demonstrate how these algorithms work and then assess their strengths and weaknesses in terms of security, performance, and use cases. The student was also required to discuss real-world applications for these algorithms and the impact of modern encryption standards.
Challenges Faced
We ensured that students fully understood the theoretical background of cryptography, but many faced challenges implementing the algorithms correctly. Understanding the mathematical foundations behind asymmetric encryption, such as prime number generation in RSA, was a hurdle for some students. Additionally, balancing the trade-offs between encryption strength and computational efficiency posed problems, particularly in performance-critical applications.
Our Solution
We provided detailed explanations of each algorithm’s theoretical foundations, followed by code samples and exercises for implementation. Students were given practical scenarios where they could apply these algorithms, such as encrypting and decrypting files or securing communications. To reinforce the importance of performance and security, we guided them on benchmarking and analyzing the impact of different key sizes and algorithm choices on system performance.
Results Achieved
The students successfully implemented cryptographic algorithms and demonstrated a good understanding of both the theoretical and practical aspects of encryption. Their code was functional and secure, and they provided insightful analysis on the trade-offs between different algorithms in real-world contexts. Students were able to discuss key concepts like key management, certificate authorities, and secure communications in detail.
Client Review
I found this assignment to be challenging but extremely rewarding. Implementing cryptographic algorithms from scratch gave me a deep understanding of how they work and how they are applied in real-world security scenarios. The performance analysis helped me see the practical implications of different encryption methods. The guidance provided was excellent, and I now feel much more confident working with cryptography in both software development and security contexts.
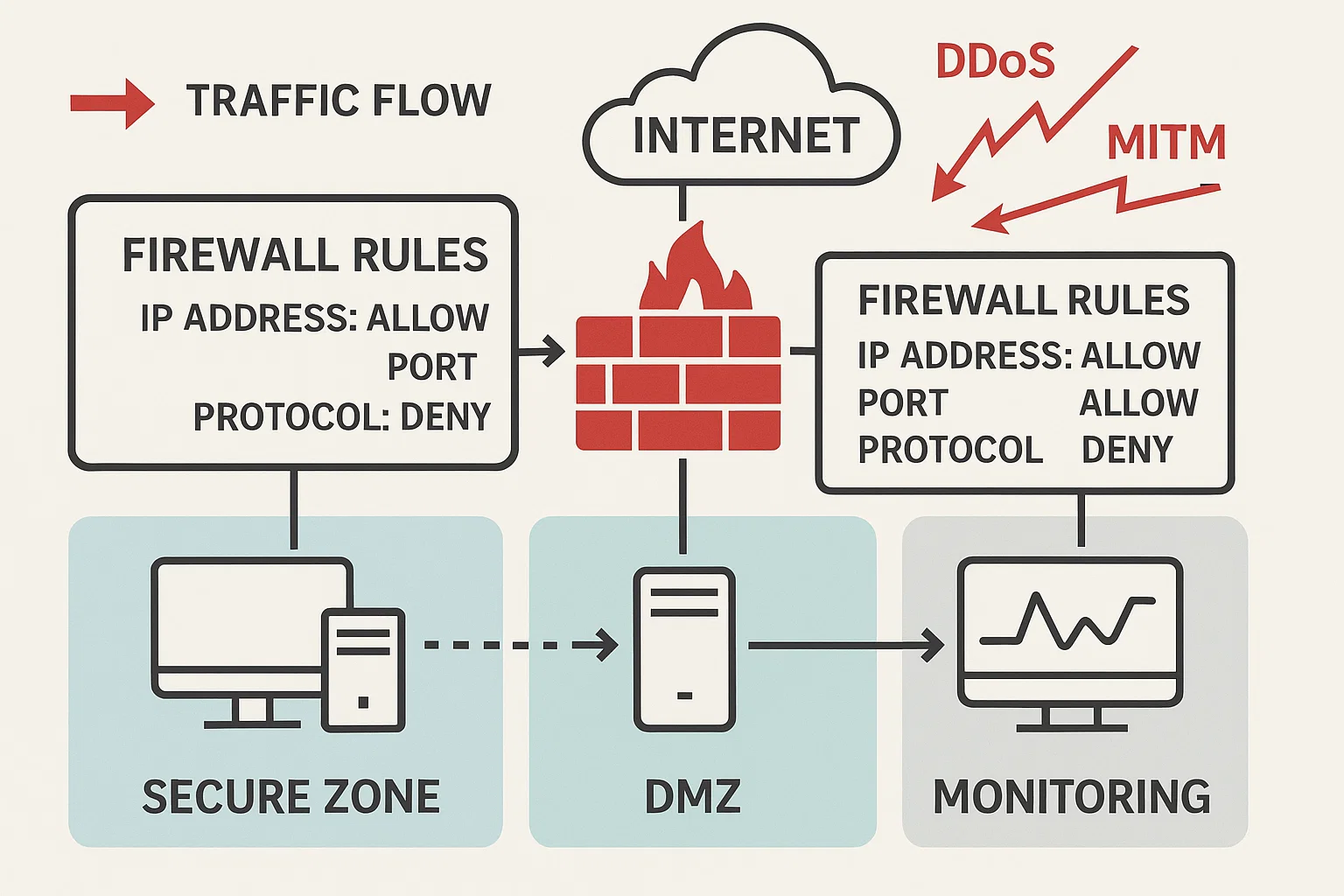
Network Security and Firewall Configuration
Network Security and FirewallsClient Requirements
The student needed to configure a firewall to secure a network from potential threats. The task required setting up rules to allow or block traffic based on IP addresses, protocols, and ports, using either a hardware or software-based firewall. The student also needed to implement strategies for defending against common network-based attacks such as DDoS, man-in-the-middle (MITM), and port scanning.
Challenges Faced
We faced complications in ensuring that students understood how firewalls operate in different network environments. Some students initially struggled with the complexity of configuring firewall rules, especially when dealing with complex network setups and advanced security features like NAT (Network Address Translation) and VPNs. Additionally, simulating and testing real-world attacks without disrupting the network setup proved to be a tricky challenge for some.
Our Solution
We provided detailed tutorials on firewall types (e.g., stateful, stateless, application-level) and practical exercises on configuring rules for both inbound and outbound traffic. Students were shown how to test firewall configurations using tools like Nmap and Wireshark. We also introduced concepts like intrusion detection systems (IDS) and intrusion prevention systems (IPS), showing how these systems complement firewalls in providing defense-in-depth.
Results Achieved
The students successfully configured firewalls, setting up rules that effectively blocked unauthorized access and mitigated common network attacks. Their reports demonstrated an understanding of network security fundamentals, and they were able to explain how firewalls fit into broader security strategies. The students were also able to test their configurations in realistic attack scenarios, ensuring that their setups were both functional and secure.
Client Review
This assignment really helped me understand how to secure networks at a granular level. Configuring firewalls and defending against network attacks gave me a practical understanding of how to implement security measures in a real-world environment. The hands-on labs and tools provided allowed me to test and refine my skills. I now have a stronger grasp of network security and how firewalls fit into an overall defense strategy.
Security Protocols and Secure Communication
Secure Communications and ProtocolsClient Requirements
The student needed to demonstrate the implementation of secure communication protocols, such as HTTPS, TLS, and VPNs. The task required setting up a secure communication channel between two devices and ensuring confidentiality, integrity, and authenticity of the transmitted data. The student was asked to analyze and compare different protocols, discussing their advantages, vulnerabilities, and use cases.
Challenges Faced
We faced challenges ensuring that students understood the underlying mechanisms of secure communication protocols and could implement them correctly. Some students had difficulty configuring certificates and setting up TLS securely, particularly in terms of key exchange and avoiding common vulnerabilities like weak cipher suites. Additionally, setting up VPNs and understanding their role in securing communication channels required careful consideration.
Our Solution
We provided students with resources on the theoretical aspects of security protocols and guided them through the practical steps of implementing secure communication. This included setting up TLS for HTTPS connections, configuring VPN tunnels, and generating and managing certificates. Students were encouraged to analyze the security properties of each protocol, understanding how encryption, hashing, and digital signatures work together to ensure secure communication.
Results Achieved
The students successfully set up secure communication protocols and demonstrated their understanding of how to secure data transmissions over the internet. Their implementation of HTTPS, TLS, and VPNs showed a practical grasp of secure communication principles. Students were also able to explain the strengths and weaknesses of each protocol and how they are used in real-world systems.
Client Review
Setting up secure communication protocols was a great learning experience. I now have a much deeper understanding of how data is securely transmitted over the internet. Implementing HTTPS, TLS, and VPNs gave me hands-on experience with technologies that are crucial in securing online communications. The assignment helped me see the practical challenges of maintaining secure communications, and the knowledge I gained will be invaluable in future projects.
