Expert Assignment Solutions with 100% Guaranteed Success
Get Guaranteed success with our Top Notch Qualified Team ! Our Experts provide clear, step-by-step solutions and personalized tutoring to make sure you pass every course with good grades. We’re here for you 24/7, making sure you get desired results !
We Are The Most Trusted
Helping Students Ace Their Assignments & Exams with 100% Guaranteed Results
Featured Assignments
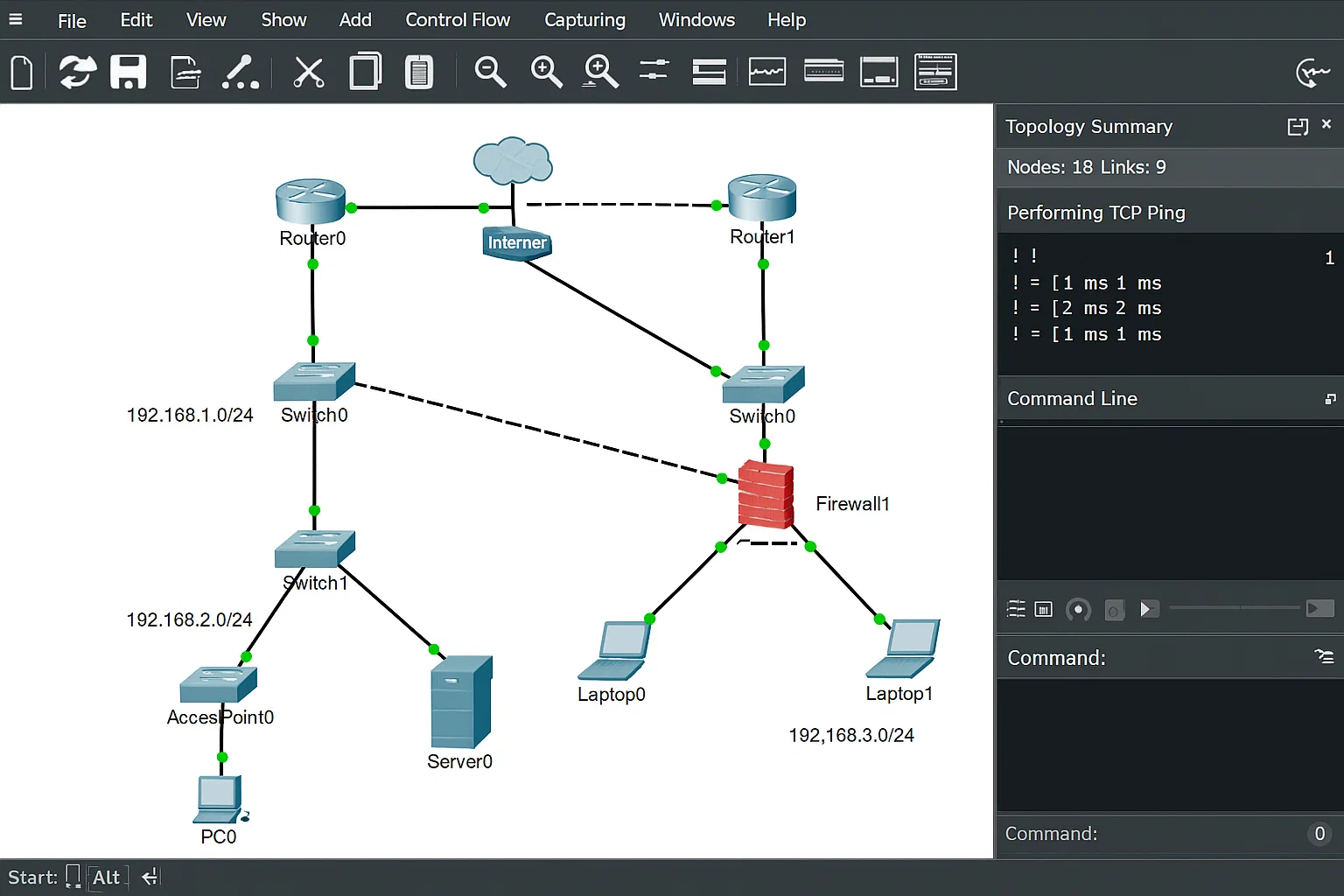
Network Topology Design and Simulation
Networking FundamentalsClient Requirements
The student needed to design a network topology for a small-to-medium-sized enterprise. They were tasked with creating a detailed diagram of network components, including routers, switches, firewalls, and access points. The student also wanted to simulate this network using a network simulation tool like Cisco Packet Tracer or GNS3 to validate connectivity, performance, and fault tolerance. The goal was to demonstrate their understanding of network design, including subnetting, IP addressing, and network segmentation.
Challenges Faced
We ensured that students properly understood the intricacies of network segmentation and subnetting, which can often lead to mistakes in IP addressing. There were complications handling network traffic flows and configuring devices to ensure that all components interacted as expected. Additionally, some students struggled with ensuring fault tolerance and simulating network failures to test the resilience of their design.
Our Solution
We provided step-by-step tutorials on designing efficient network topologies, including how to choose between different network designs based on performance and scalability needs. Students were also guided in configuring routers, switches, and other network devices to test connectivity. Furthermore, we emphasized the importance of redundancy in network design, such as using multiple paths between devices to ensure fault tolerance.
Results Achieved
The students successfully designed and simulated a network topology that demonstrated robust connectivity, efficient data flow, and fault tolerance. Their simulations showed that the network could handle various failure scenarios without significant service disruption, illustrating a strong grasp of enterprise network design.
Client Review
My experience with this assignment was exceptional. The detailed guidance on network topology design and the simulation exercises helped me understand the core concepts of network setup, subnetting, and redundancy. The tools and resources provided were highly effective in helping me test my network design in real-time, and I’m confident that I now have a solid understanding of how enterprise networks operate.
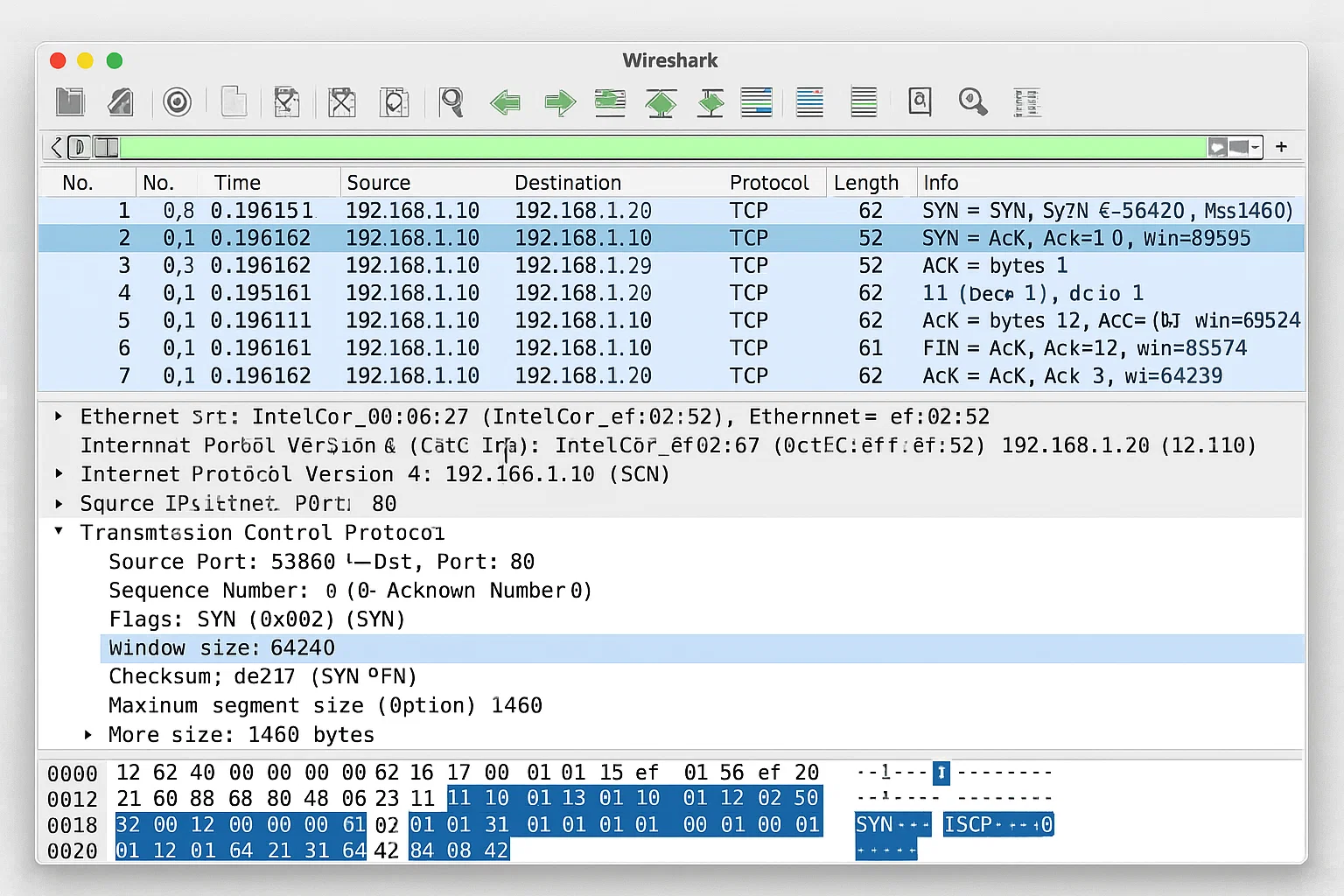
TCP/IP Protocol Stack and Packet Analysis
Network Protocols and AnalysisClient Requirements
The student wanted to dive deeper into the TCP/IP protocol stack by performing packet analysis using tools like Wireshark. They were tasked with capturing and analyzing traffic between two devices communicating over a TCP/IP network. The goal was to identify key protocol layers (e.g., application, transport, network, data link) and examine the structure of each packet, focusing on header fields, flags, and data segments.
Challenges Faced
We faced some challenges ensuring that students understood the intricacies of the TCP/IP stack, especially distinguishing between different protocol layers and identifying relevant fields within the packet headers. Some students had difficulty capturing the correct type of network traffic and analyzing complex packet details such as flags, sequence numbers, and acknowledgments.
Our Solution
We provided comprehensive guides on using packet analysis tools like Wireshark, including instructions on how to capture specific traffic, filter packet types, and examine the protocol layers. Students were given predefined tasks to analyze specific communication scenarios, such as a file transfer or a web page request, and identify key aspects of the communication process in terms of the TCP/IP protocol stack.
Results Achieved
The students successfully captured and analyzed network packets, demonstrating a clear understanding of the TCP/IP protocol stack. They were able to identify the structure of packets, interpret flags and sequence numbers, and explain the behavior of each protocol layer in the context of real-world communication.
Client Review
I had a truly insightful experience working on this assignment. The packet analysis using Wireshark gave me a firsthand look at how data is transferred across the network and how each layer of the TCP/IP stack functions. The task really helped me solidify my understanding of the protocols involved in network communication. The resources and guidance provided were perfect for making the analysis process both engaging and educational.
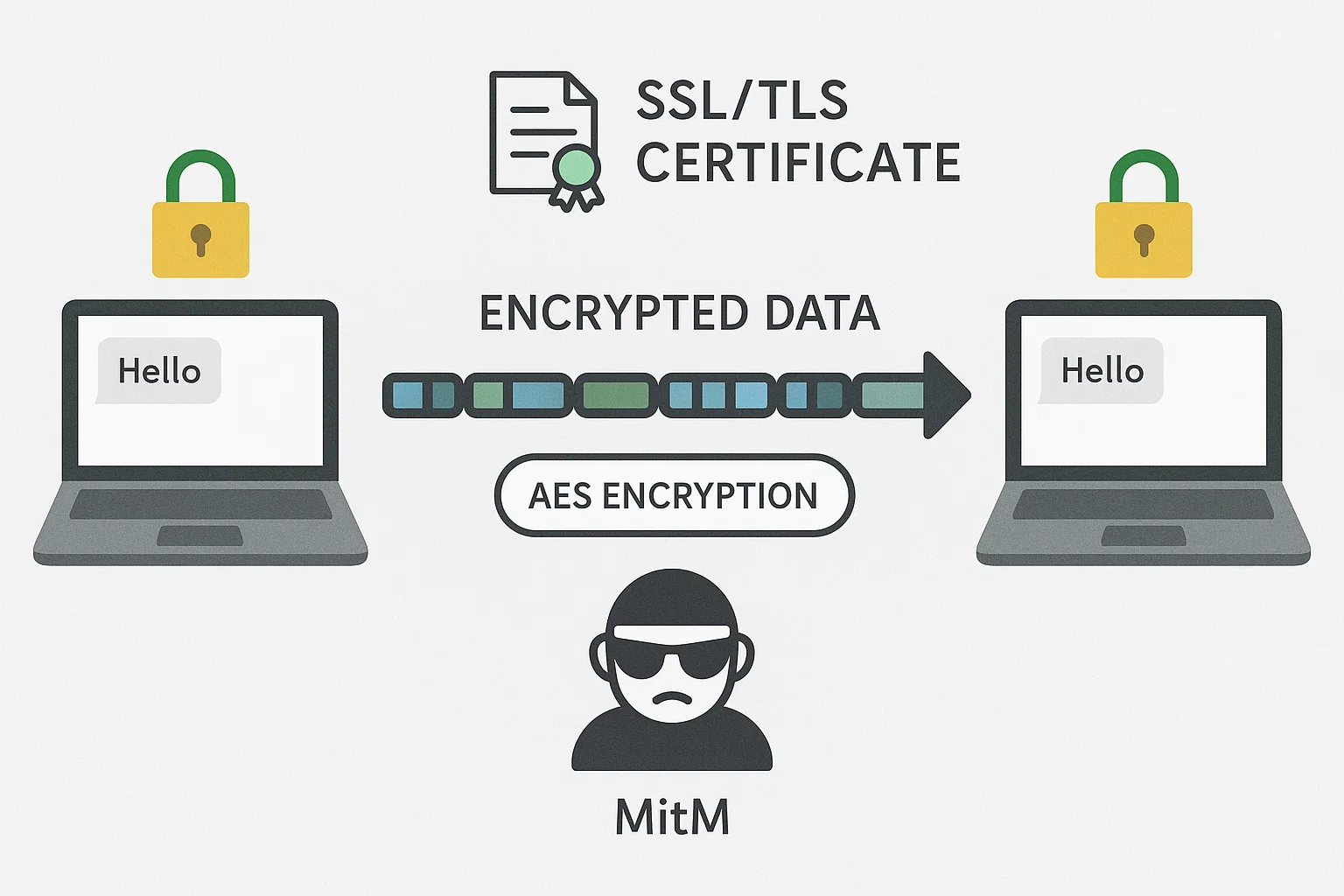
Network Security and Encryption
Network Security and CryptographyClient Requirements
The student needed to demonstrate an understanding of network security by implementing encryption methods to secure communication between two devices. They were tasked with setting up a secure communication channel using protocols such as SSL/TLS, and encrypting sensitive data using methods like AES. The student also needed to simulate attacks, such as Man-in-the-Middle (MitM), and demonstrate how encryption mitigates these vulnerabilities.
Challenges Faced
We faced complications handling the different encryption techniques and ensuring that students applied them correctly in a real-world network setup. Some students struggled with configuring SSL/TLS certificates and setting up secure communication between devices. Simulating network attacks and understanding their implications for network security proved to be challenging for many.
Our Solution
We implemented a guided exercise where students set up secure communication channels between devices using SSL/TLS, configuring certificates and encrypting data with AES. Additionally, we provided simulated attack scenarios, such as a Man-in-the-Middle attack, and guided students on how encryption could mitigate such threats. Practical examples and exercises helped students see how security protocols function in real-world network environments.
Results Achieved
Students successfully configured secure communication channels, implemented encryption techniques, and demonstrated their ability to defend against attacks using SSL/TLS and AES. They clearly understood how encryption enhances network security and protects data integrity during transmission.
Client Review
This assignment was incredibly engaging and practical. It gave me hands-on experience with securing communications over a network and understanding the underlying encryption technologies that protect sensitive data. The simulated attacks and how encryption defended against them were very eye-opening. The guidance provided was clear, and I feel much more confident in my ability to implement network security solutions.
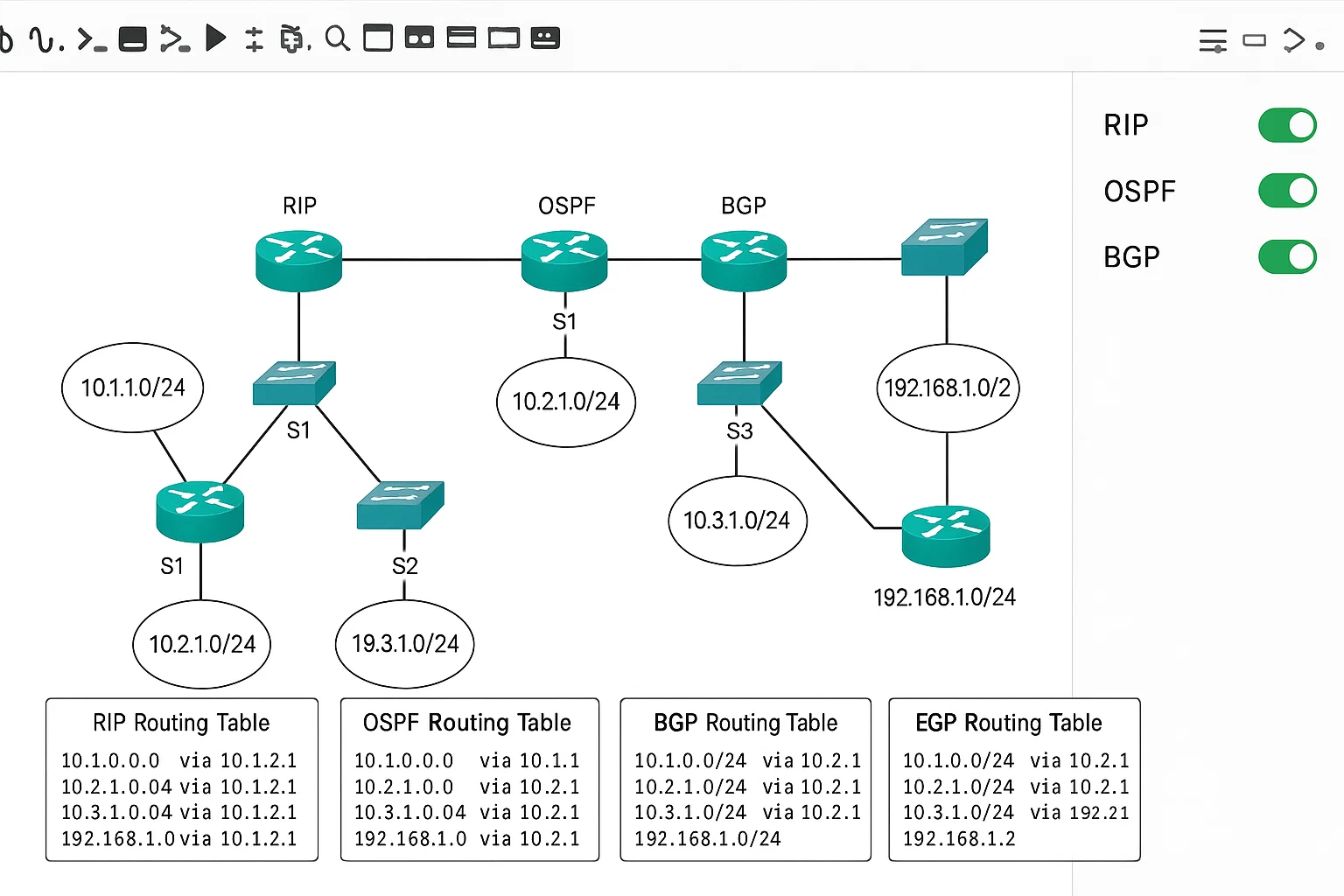
Routing Protocols and Network Configuration
Advanced Routing and Network ConfigurationClient Requirements
The student wanted to learn and implement dynamic routing protocols, including RIP, OSPF, and BGP. They were tasked with configuring these protocols on routers to enable dynamic routing across multiple subnets and simulate various network topologies. The goal was to ensure proper network routing and demonstrate how each protocol behaves under different network conditions.
Challenges Faced
We ensured that students understood the key differences between the routing protocols and their respective configurations. Some students faced difficulties with complex routing table configurations and understanding how each protocol adapts to network changes. Additionally, troubleshooting routing issues when the network topology changed or when protocols failed to converge was a challenge.
Our Solution
We provided detailed instructions on configuring each of the three routing protocols, explaining their differences, advantages, and ideal use cases. Students were given multiple network topologies to configure and test, and they had the opportunity to troubleshoot routing issues. We also offered guidance on simulating network failures and observing how each protocol handles such events.
Results Achieved
The students successfully configured dynamic routing protocols and demonstrated how the network adapted to changes in topology. They were able to configure RIP, OSPF, and BGP on routers, troubleshoot routing issues, and explain the differences in behavior between the protocols in various network scenarios.
Client Review
My experience with this assignment was highly rewarding. The hands-on approach to configuring and testing dynamic routing protocols was invaluable. I gained a much deeper understanding of how these protocols work in practice and how they respond to network changes. The troubleshooting exercises were particularly helpful, and the support I received throughout the process ensured I was able to complete the tasks successfully.
